Today, I feel like talking about remote work and remote executions. I have read a lot of articles detailing the pros and cons of remote work. I tell you one thing, even as it is a sensitive topic, so is the remote-exec function in Terraform. One must be very careful with the execution of both in their different contexts.
I’ve had way too many chats about the limits of Infrastructure as Code (IaC). It’s like every time I think I’ve got it figured out, there’s a new quirk waiting to throw me off. IaC is like that one friend who always surprises you, for better or for worse. But hey, at least it keeps things interesting, right?
By the way, in Terraform, the remote-exec provisioner is all about modeling specific actions that can be executed on a remote machine post-provision. Just as it is labeled a last resort on Hashicorp’s documentation page, I will take the advice literally. This is due to the limitations and security considerations of its requirements for a successful deployment:
- Access to your servers
- Issuing credentials to log in
- Ensuring the prerequisite external software is installed
One of the specific use cases where provisioners are not the first recommendation, but if by luck there is no option, then you can use a provisioner as the Post-Deploy Configuration management software.
To illustrate this, I have created a simple situation where a business needs a generic build of a NGINX server. I have added the provisioner connection block inside a null resource as you can see below
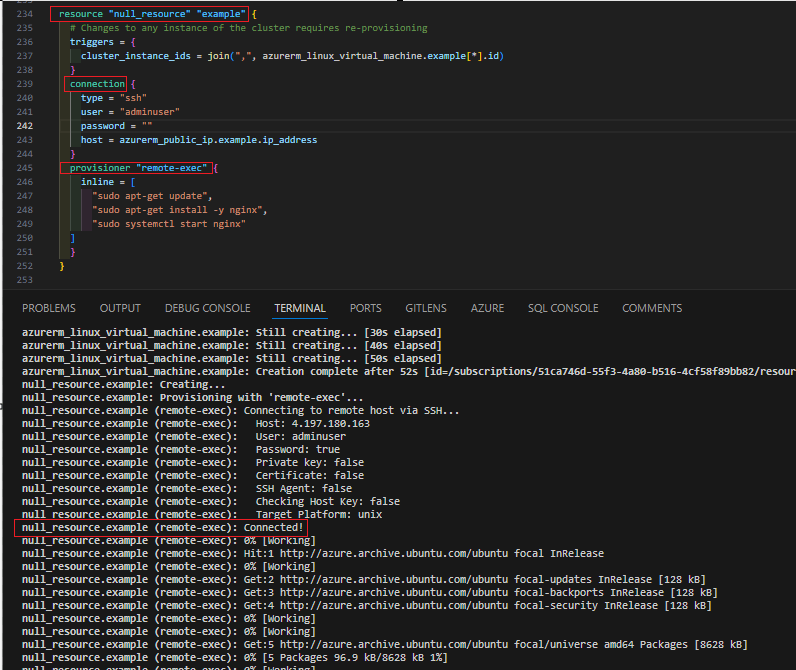
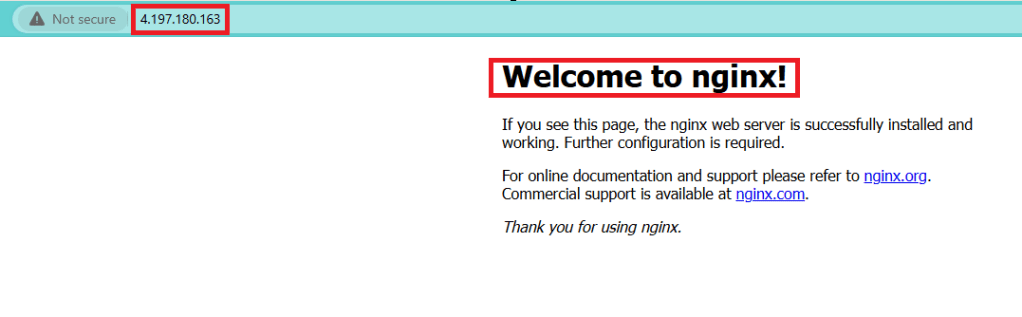
Of course, I ran the terraform trio – “init”, “plan”, “apply” to test it out on my terminal.
You would need the connection instance, if your aim is to achieve a remote execution, where the connection carries the same operational detail as if you were connecting to the already provisioned device.
With the concerns listed above by above, I decided there might be better ways to secure your deployment – ADO!
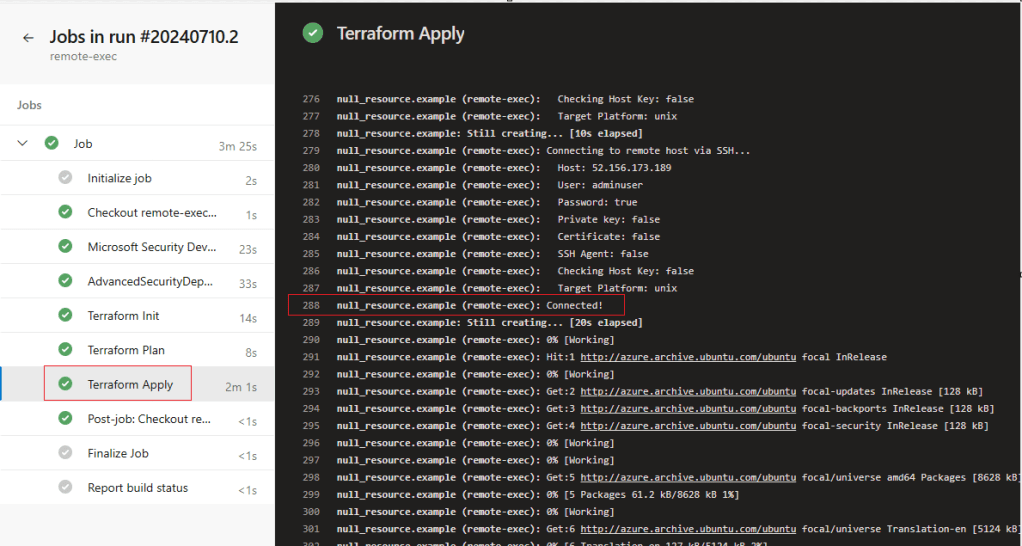
With all the features given in the Azure DevOps, you can work your way securing your deployment, even of this nature.
In this configuration, the null_resource with the remote-exec provisioner handles the installation of NGINX on a Linux virtual machine. This showcases a specific use case where, despite the limitations and security considerations, the remote-exec provisioner can be a viable option when no better alternatives are available.
In conclusion, just as with remote work, it’s essential to carefully evaluate and manage the use of remote-exec to avoid potential pitfalls and ensure a secure, effective deployment
Visit my Github to see my full code – Github
What has been your experience on using the provisioner function?
Hope to read from you soon.

Leave a comment